HoloLens got to be one of the cooler devices out there, but probably also one of the lesser-known devices how to manage.
What is a HoloLens really?
HoloLens is Microsoft’s device aimed for Mixed Reality, but at heart, it’s actually a Windows-based device but done in a more modern way. This means that the support for legacy protocols is limited, but also that the level of built-in security is maybe a bit higher than on your Windows-based PC. You can read more about the HoloLens as a platform here.
Given that it’s a Windows device, we can manage it using basically the same policies in Microsoft Endpoint Manager (MEM) as you would for the rest of your Windows devices. A lot of baseline profiles could be re-used (or duplicated) with ease which simplifies the configuration a bit.
There are a few things to keep in mind when it comes to Microsoft HoloLens 2, which has had an impact on the designs and implementations in my experience.
- It doesn’t support EPP/EDR software of any kind
- You can only run UWP based applications
- You will need additional licenses to run e.g. Remote Assistance
HoloLens 2 as a kiosk
There are a lot of different applications and ways to implement and use a HoloLens 2. In this post, I’ll focus on how to set up the HoloLens 2 as a multi-app kiosk, but with user sign-in, using Microsoft Endpoint Manager.
Importing the device into Windows Autopilot
If your vendor or retailer didn’t import the HoloLens hardware ID for you, you can do this by following these four simple steps:
- While the HoloLens 2 device is powered on, press and release the Power and Volume down buttons together to trigger the hardware ID and diagnostic log collection process.
- Connect the HoloLens 2 device to a PC using a USB cable so that it shows up in File Explorer.
- Browse to Internal Storage > Documents and extract AutopilotDiagnostics.zip. This file/folder will contain a CSV file with a a file name that begins “DeviceHash…”.
- Upload the CSV file to the Windows Autopilot service
In order to simplify our management a bit and be able to create a dynamic device group with only HoloLens devices, assign a GroupTag to the device such as “Hololens”.
Creating a device group for HoloLens
Like all things in device management, we are really dependent on groups. In this case, we will use a device group to target only our HoloLens devices.
You can create a new Azure AD group by selecting Groups in the left hand side menu in the MEM portal. Then select “New group“.
Give your group a good name and select “Dynamic Device” as Membership type.

Next, click “Add dynamic query” at the bottom and add the following rule syntax, but replace the word Hololens used here with the name of your GroupTag.

(device.devicePhysicalIds -any _ -eq "[OrderID]:Hololens")
Click Save followed by Create to finish the creating of the group.
Setting up enrollment
First off, we need to create a new Deployment Profile for the HoloLens platform.
You will find the Deployment Profiles by navigating to Devices > Windows > Windows Enrollment and selecting Deployment Profile.

When you have selected the Deployment Profiles card, select “+ Create Profile” and choose HoloLens as the platform.
Give your profile a name in the Basic tab and press next. On the “Out-of-box experience (OOBE)”, you can really only have to change the name template if you are looking to use custom names for your HoloLenses. In my example, I’ve left all values to default. Press next to move to the next tab.

On the Assignment tab, select your HoloLens device group and press next.

Review your settings and hit Create to finish the creating of the deployment profile.
Creating a Filter for HoloLens
To make sure that we only target settings deployed towards users to their HoloLens devices, we need to create a filter we will use later on.
Navigate to Tenant administration > Filter. Create a new filter by clicking “+ Create” in the top ribbon. Give your filter a name, such as HoloLens, and select Windows 10 and later as the platform.

Since filters are kind of like dynamic groups, we need to add a syntax. The easiest way I’ve found to include HoloLens devices is to use our Deployment profile name, the attribute is called EnrollmentProfileName on the device. Enter the name of your Deployment Profile in the Value field.

Click next, then review and create the filter.
Configuring kiosk mode
You could basically already enroll your devices now and be done, but it will be like an unconfigured PC, your end-user will miss vital settings and applications.
Since this is a Windows-based platform, you can reuse or duplicate profiles you already have for Wi-Fi, certificates, and such. Not all profiles make a whole lot of sense to use on the HoloLens (such as settings for the Office suite or Chrome browser to give some examples).
The profile we need to create to set up the Kiosk-mode on HoloLens is a profile based on the Kiosk template.
Go to Devices > Windows > Configuration profiles and create a new profile by pressing “+ Create profile” in the top ribbon. Select Windows 10 and later as platform and Templates as Profile type. Scroll down and find the Kiosk template and click create.

As always, give your profile a name based on your naming convention on the basic tab and press next.

Based on your scenario, select either “Single app, full screen” or “Multi app kiosk” as kiosk mode and select “No” on the question if device is running S mode.

In my scenario, I will configure that users will use the device using their Azure AD accounts. Since I have to specify a group with eligible users, I’ve in my setup used a group containing most of my users meaning that all my users are allowed to sign in to the HoloLens. You can easily assign this to either a group of users or even a specific user. You can also add additional groups and/or users. Depending on your scenario, you can make different choices here.

Next up is to select what applications we will run on the device. This can be done by either selecting built-in applications or applications distributed through MEM. Keep in mind that Win32 applications DO NOT WORK on the HoloLens when selecting applications.
If you want to add built-in or system applications, this is done by adding the AUMID of the application. You can find all the HoloLens 2 applications AUMID on this MSFT Docs site.
In this example, I will add one built-in application and one store app. You add apps by pressing the “Add…” button under the Browser and application section.
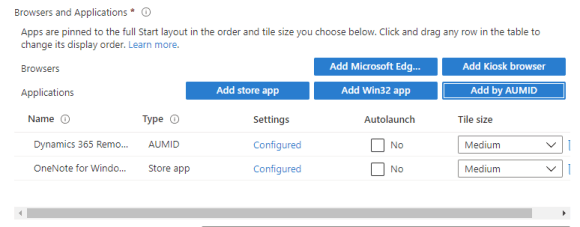
When adding a app by using AUMID, you give the application a name (preferably what it’s called in the reference document) and the AUMID for the application.

When adding a store app, MEM will list the apps you have available for distribution. Also, keep in mind that you will need to make sure to target the application distribution towards the HoloLens group.

Leave the rest of the settings to the default value and click Next.

In order for the Kiosk mode to function properly when requiring Azure AD users to sign in, the profile needs to be targeted toward users otherwise nothing will happen in my experience. If you are not doing personal logins, you can target this towards a device group.
In order to not assign the Kiosk-mode to all the user’s devices, we will need to use a filter to limit what devices the profile is assigned to.
On the Assignment tab, select your group of users who will be allowed to use the HoloLens and then press “Edit filter” next to the group.

Select “Include filtered devices in assignment” and choose your filter then press Select.

Press next and leave the Application Rules to blank and review and create your profile.

Enroll and sign in!
Now it’s time to enroll your device, simply start the device and follow the on-screen instructions.
What I’ve seen is that sometimes, the kiosk mode does not kick in on the first login after enrollment. If this happens, simply sign in and out of the device, this has done the trick for me!

